CISO Diaries
How CISOs can drive a security culture change
CISOs lead the charge in cybersecurity, from fostering communications to tackling breaches. When crises hit, they're the answer, but security is a team effort, which demands a culture shift.

Mags22,
May 09
2024
Table of Contents
CISOs and their teams are in a perpetual balancing act.
From fostering strong relationships with business leaders to staying ahead of cyber threats, they're on the frontlines of risk detection, mitigation, and remediation.
And most daunting of all:
They are the ones who the entire organization looks to for answers when things go wrong.
When a breach occurs, it's the CISO and security team who must be able to answer questions like:
-
Why were systems compromised?
-
Have threats been triaged and isolated?
-
What remediations are in place?
-
What are the total financial consequences?
However, this is an impossible task to do alone. Security is ultimately a team sport. So CISOs and security teams need the entire organization committed to improving security.
This is why CISOs must be willing to influence their organization's security culture from something that's “security's job”, to a shared responsibility between all departments.
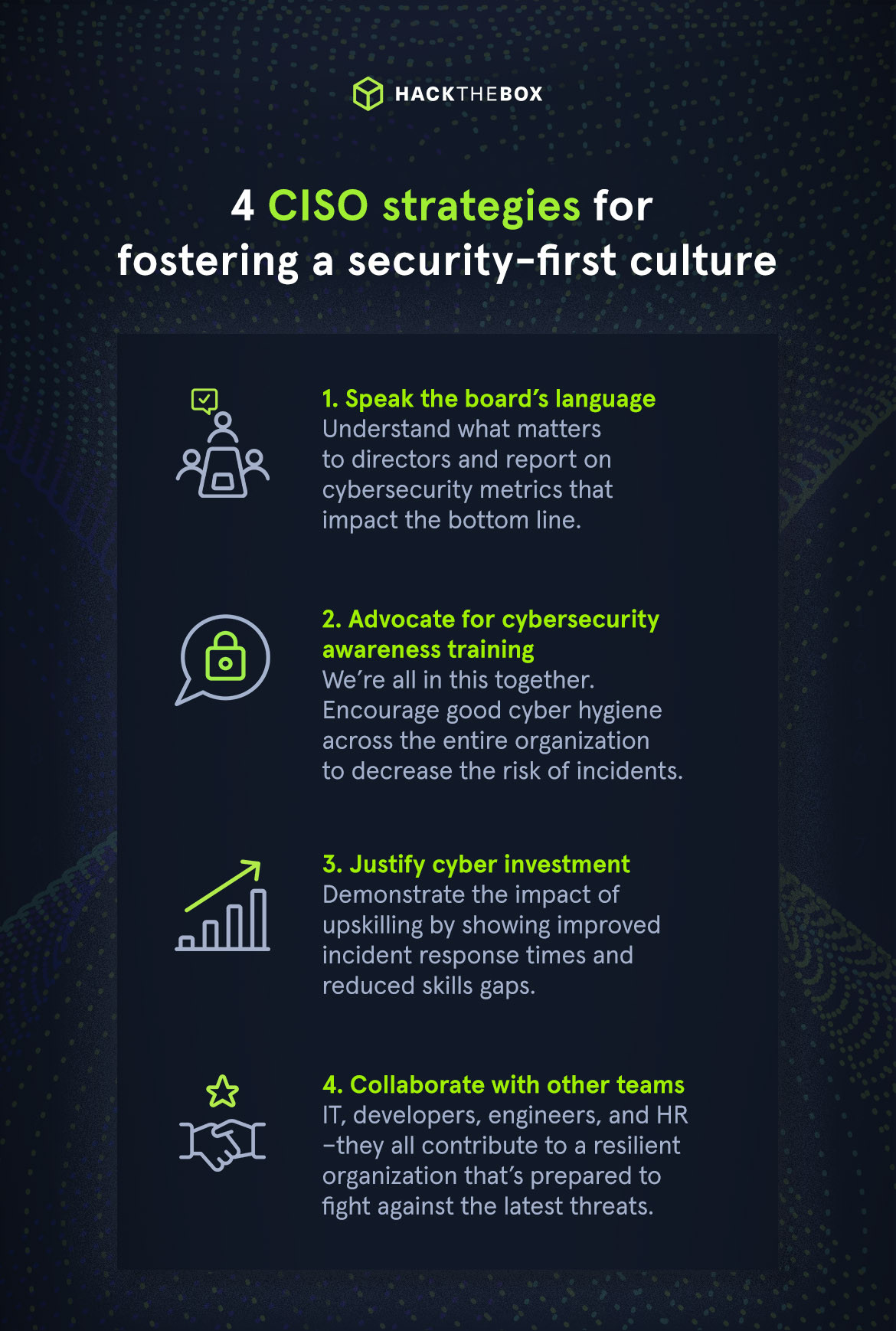
Speak the board’s language
To break down barriers between cybersecurity and the board of directors, CISOs need to understand what organization leaders care about:
-
The bottom line: money going in and out, are balance sheets healthy?
-
Risk mitigation: how can we reduce organizational risk?
-
Who’s responsible if something goes wrong?
-
How you’re perceived: are you a hurdle or a bringer of bad news? Provide solutions to problems.
There exist misunderstandings on both sides of the coin. Executive board members may underestimate the severity of cybersecurity risks and so allocate fewer resources. Meanwhile, CISOs may not report correctly to the board or connect security team activities to the broader organizational goals.
By bridging the gap and communicating effectively, board members and CISOs can achieve what’s required.
Here’s what to focus on when reporting and making your case to the board:
-
What’s the cost of a cyber attack? By defining this cost clearly, you’ll be able to make the case for cybersecurity for the business. Discuss the real cost, both monetary and also reputational.
-
How many vulnerabilities have been mitigated? Regularly track vulnerability patches in comparison to the previous report. Focus on how upskilling has helped to discover more vulnerabilities.
-
What’s your incident response speed, and how could this be reduced? As a CISO, it’s important to come up with solutions to reduce incident response speed, through awareness, upskilling, and other initiatives. For example, running incident response tabletop exercises (TTX) or assurance exercises that can measure ROI factors.
-
What return will leaders get on investment from your cybersecurity team? Think about reduced incidents, shorter response times, and fewer attacks.
Make cybersecurity awareness training compulsory
Most organizations need more cybersecurity awareness. Cybersecurity should be everyone’s responsibility, from new hires to managers, everyone should practice good cyber hygiene to help mitigate risks.
All employees should undergo cybersecurity awareness training, regardless of their department, as part of the onboarding process. To encourage buy-in from upper management, it’s worth noting that CISCO’s cybersecurity threat trends report found that at least one person clicked a phishing link in around 86% of organizations.
CISOs are responsible for creating a cybersecurity culture, so facilitating this training will place security at the forefront of employee’s minds. The first step would be to set up simple phishing email training to help employees spot real vs. fake communications.
You can go a layer deeper by engaging employees in tabletop exercises to walk teams through a hypothetical attack scenario. Within those exercises, employees across different departments can discuss how the organization would respond to identify gaps in current procedures.
CISOs should also regularly review previous security incidents with teams, to foster a culture of open communication when it comes to past mistakes. This also teaches employees how to avoid such incidents in the future.
Finally, threat intelligence should not only be shared with the cybersecurity team but also with the wider business. This helps to discover new threats to the organization's branch of industry, new attack vectors, and exposed systems.
Justify the extra investment
Upskilling is essential to ensure your cybersecurity team is threat-ready and aware of the latest vulnerabilities. Yet, this calls for ongoing investment, as one-off cybersecurity training won’t move the needle.
Blue guys always have the hardest job, they have to be right 99% of the time, hackers only have to be right 1% of the time.
Clayton Jones, Chief Technology Officer at Aperio Global, LLC, speaking on HTB’s federal workforce development webinar.
Training blue teams on red tactics, techniques, and procedures (TTP) will make them better prepared to defend, dramatically reducing mission risk, and vice versa.
CISOs need to be able to justify this extra investment by choosing an upskilling platform that aligns with their company goals and reduces risk. At Hack The Box, we recommend starting this process by benchmarking your team's skills using an engaging Capture The Flag (CTF) activity. This tests teams across offensive, defensive, and cloud environments.
Once completed, team leaders can analyze the CTF results to identify skill gaps and areas for development. At HTB, we make this easy by mapping capabilities against MITRE ATT&CK & NIST NICE frameworks. This makes reporting back to the board with results assessing a cybersecurity team's performance, skills, and effectiveness against industry standards much simpler.
Now, the extra investment can be justified with clearly mapped areas to focus on, aligning the organizations with industry best practices whilst enhancing incident response preparedness.
What about reporting on upskilling results? We recommend tracking the following:
-
% of increased time spent on upskilling.
-
% of increased team engagement level.
-
% of decreased response time or incident recovery.
Track progress with Hack The Box Enterprise Platform
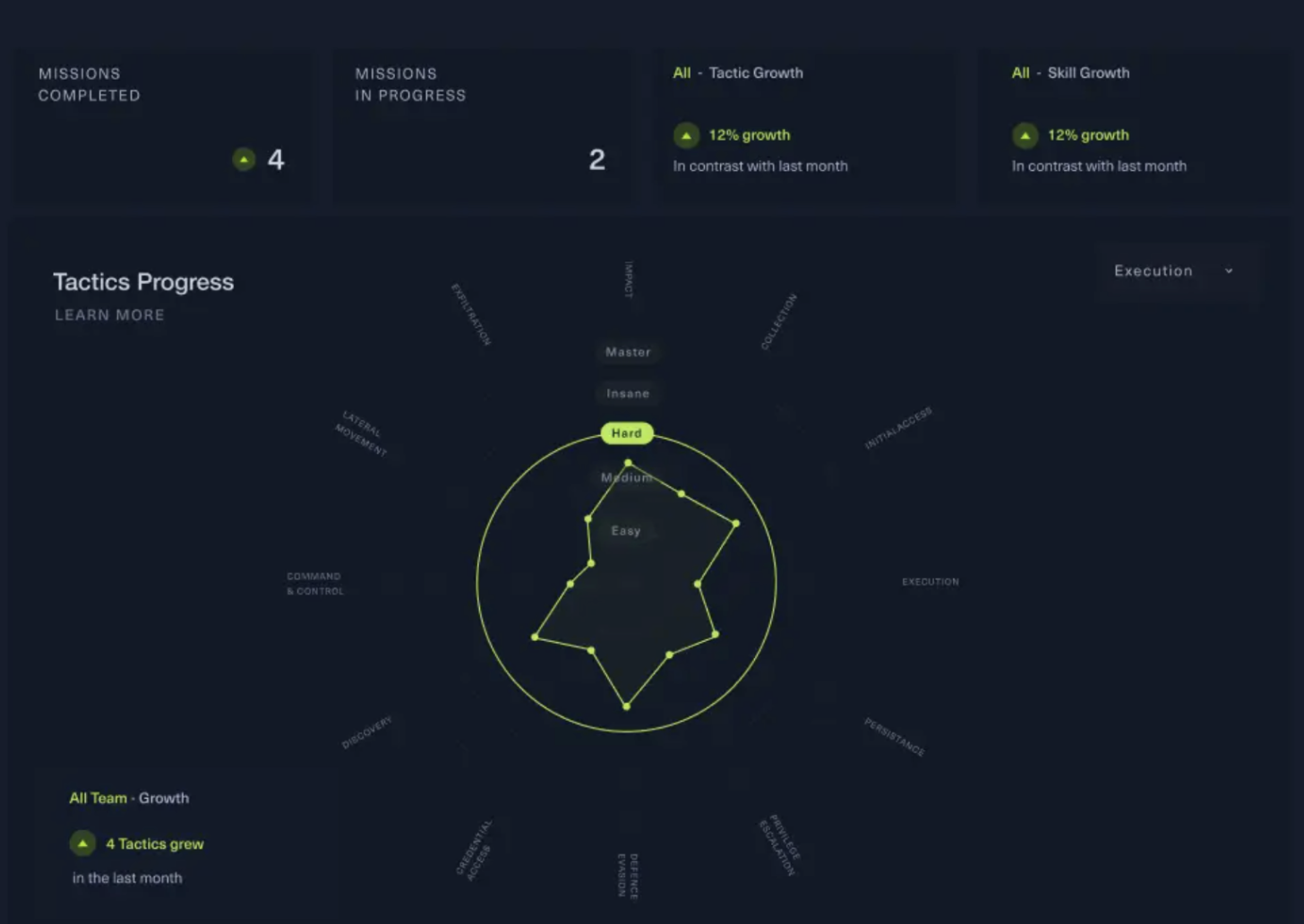
Understand the impact upskilling has on your team and their engagement levels with HTB’s tracking and reporting features:
-
Monitor engagement on a weekly and monthly basis.
-
Search and assign content based on MITRE ATT&CK frameworks, enabling you to track progress on different techniques and tactics.
-
Assign content based on skill gaps found, making upskilling tailored to the individual.
-
Engage team members whilst improving organizational resilience.
Entering a new era of cybersecurity
CISOs are no longer independent entities that work within their bubbles. They now have more opportunities than ever to speak the same language as the board and justify extra investments. And the C-suite is listening. As cybersecurity only becomes more important by the year, leaders are aware of just how dangerous a lax cyber operation can be.
This doesn’t mean it’ll be easy, as compliance remains stringent, new threats emerge, and the skills gap looms. However, by fostering a cybersecurity culture of collaboration and awareness, CISOs can greatly impact their organization’s security posture.
|
Dan Magnotta (Mags22), HTB Federal Business Development & Capture Manager, Hack The Box Dan Magnotta is an accomplished professional in cybersecurity and intelligence operations with more than a decade of experience in the military and private sectors. His career began with dedicated service to the U.S Department of Defense, where he played critical roles in the U.S. European Command and U.S. Special Operations Command Europe, contributing significantly to cutting-edge cyber strategies. In addition to his civilian role, he serves as an LCDR in the U.S. Navy Reserve, showcasing his leadership and dedication as an Executive Officer for a Navy Reserve Unit. His expertise in cybersecurity, operational analysis, and strategic planning is extensive. At Hack The Box, he tailors solutions to meet the unique requirements of government agencies and organizations worldwide, leveraging his deep understanding of both military and civilian cybersecurity needs. |